This page contains:
Unit 1 - Types And Components Of Computer Systems
Unit 3 - Storage Devices And Media
and
Unit 4 - Networks And The Effects Of Using Them
Unit 1 - Types And Components Of Computer Systems
Hardware
A physical component of a computer system (everything you can touch).
Internal hardware devices
Processor. Also called CPU (Central Processing Unit) is the brain of a computer. It is the part of a computer that carries out calculations, executes instructions and processes data.
Motherboard. A board that connects the main components of a computer.
RAM (Random Access Memory). Is memory that is used to store currently active programs and data. The more RAM that is available to the computer, the more data and programs can be used at the same time.
ROM (Read Only Memory). Memory that, once it has been written to, can no longer be changed. ROM stores the instructions to boot (start) the computer.
Video card. Generates the signals needed to display the output image from the computer.
Sound cards. Generates the signals needed to output sound from the computer to a speaker.
Internal hard disk drives. Secondary storage device.
External hardware devices.
Monitor
Keyboard
Mouse
Printer
External storage devices (USB stick, Hard Disk, etc.)
Software
Programs that control the operation of a computer or process electronic data.
Applications software. The software that you use to do your work and to entertain yourself.
Word processing
Spreadsheets
Database Management Systems
Photo-editing software
Video editing software
System software. Controls the way the computer works and tells it what to do.
Compilers. Are programs that translate computer code written in a high-level language into low-level language (e.g. machine code)
Device drivers. Are the programs that
Operating systems. Software that manages hardware and software resources and provides common services for computer programs.
Utilities. Examples:
Hard disk formatter.
Backup software
File compression
Virus checker
Questions:
1. If I want to write a letter of complaint to my bank what type of software would I use? Application or System software?
2. If I want to check if my computer has a virus what type of software would I use? Application or System software?
3. If I want to do a collage with all my photos of 2016, what type of software would I use? Application or System software?
4. If I want to create a mashup video what type of software would I use? Application or System software?
5. If I want to backup all the data I have stored on my computer, what type of software would I use? Application or System software?
6. What does it mean to compress a file?
7. If I want to compress all my files from 2016, what type of software would I use? Application or System software?
Main components of computer systems
CPU (Central Processing Unit)
Input/output devices
Secondary backing storage
Main memory: ROM and RAM
Differences between RAM and ROM:
Random Access Memory (RAM):
-Volatile. Information IS lost when the computer is turned off.
-Information stored in RAM can change.
-Stores data and programs currently in use.
Read Only Memory (ROM)
-Non-volatile. Information is NOT lost when the computer is turned off.
-Information stored in ROM cannot be modified by the user.
-Stored instructions that tell the computer how to start up.
Operating systems
Command Line Interface (CLI). A command line interface allows the user to interact directly with the computer system by typing in commands. Advantages and disadvantages.
Some CLI commands are: copy (copy files), del (delete files), md (make directory (directory means folder)), rmdir (remove an empty directory)
Graphical User Interface (GUI). It makes use of pictures, graphics and icons. Advantages and disadvantages.
Types of computer
Personal/Desktop computer. General purpose computer made up of a separate monitor, keyboard, mouse and processor unit.
A personal computer can be used as:
- Standalone computer: can operate without connecting to other computers and it is used by one person at a time. It is used to perform tasks such as school work, household accounts, gaming.
- Networked computer: part of a group of connected computers. They are used to share resources such as printers.
Laptop computer. Computer where monitor, keyboard, pointing device, processor unit and battery unit are combined in a single device. Their uses are the same as personal computers.
They can also be used as standalone or networked computers.
Tablet computer. Device with touch screen; has a virtual keyboard which uses touch screen technology; access to the internet is through 3G/4G or Wi-Fi; uses solid state memory which is limited in size.
Tablets are used for internet access, entertainment (movies, music, games), and use of application software.
Smartphone. Communication device similar to a tablet but usually much smaller; uses touch screen technology and 3G/4G or Wi-Fi to connect to the internet or to make phone calls or send messages.
Advantages and disadvantages of computer types:
Desktop
Advantages
lightweight and self-contained, therefore portable and no trailing wires
lower power consumption than desktop computer
can be used anywhere if there is a Wi-Fi hotspot
Disadvantages
easier to break or steal since portable
limited battery life or need to carry heavy adaptor
keyboards and pointing devices can be awkward to use
Tablet
Advantages
have better specification, for example, a faster processor, for a given price than the others
since it is not portable, it is less likely to be damaged/stolen
more stable internet connection since it is often hard-wired
Disadvantages
not portable due to separate components being used
because they aren't portable, it is necessary to copy data/files on to memory sticks or to the cloud
more cumbersome due to trailing wires, desktop space
Smartphone
Advantages
very fast 'power up'
fully portable; small and light
no need for input devices since uses touch screen and Apps
uses solid state devices; therefore, produces little heat
Disadvantages
limited memory
typing on a touch screen can be very slow and error-prone
transfer of files can be a slow process
need to use an App store for most software
Laptop
Advantages
always on your person since it is small and lightweight
can make phone calls as well as 'surf' the net
can be used anywhere since uses Wi-Fi and 4G/5G
battery life is much longer than laptops
Disadvantages
small keyboard makes data entry slow and error-prone
Apps, such as camera App, can drain battery quickly
small memory size
not all website features can be displayed
slow data transfer
Revision
Fill in with the missing words:revision
Impact of emerging technologies
Describe how emerging technologies are having an impact on everyday life
Artificial Intelligence
Those with disabilities can use voice activated systems, such as Siri or Google Now, to search the web, message family and friends, etc.
The development of self-driving cars may mean that those with disabilities will also be able to travel independently in a car. It may also make the taask of driving a car safer, by removing the element of human error.
The level of entertainment provided by games is much greater. This is because an enemy or opponent in a game can be made more challenging to beat.
It can be used to create expert systems that allow easy diagnosis or problem solving of issues that require expert knowledge.
However, artificial intelligence is not without its issues:
In the case of self-driving cars, there is a debate about who should pay in the event of an accident on the road, where the self-driving car is at fault. Should the user have to pay? This issue is as yet unresolved.
Voice activated systems are improving, but they still suffer from lots of input errors. If artificiall intelligence is dependent on a voice-activated system, it will be limited by the abiity of this system.
Artificial intelligence is only as good as its programming. If there are errors in the programs that allow the intelligence to be created, then it will not operate correctly.
Biometrics
Biometrics is the use of technology that tracks user values. This could be as simple as their heart rate with fitness devices, or it could be voice recognition software, fingerprint and iris recognition or even recognition of DNA patterns.
Biometric technology is incredibly personalised because of the data it takes in and stores. This can cause issues:
Very personal details are stored about users. These could be used against them if someone were able to hack into the database where the data is stored. In fact, the database could be abused and have data values replaced, locking original users out and giving access only to those who hacked into it.
There isn't anything stopping a user from presenting fake biometric material, such as a fake fingerprint or a recording of a voice command. These would need to be very high quality to be undetected, but it is possible.
Some people feel that their human rights are being violated through the collection and use of their biological data for security reasons. They feel that it is a huge invasion of their privacy to have this kind of data stored and used in this way.
Vision enhancement
Vision enhancement is normally provided in the form of a type of glasses or lenses. This alters the stimulus that enters through the eyes and filters it in a way that can enhance a person's vision. The glasses or lenses can be tailored to the person and their current level of vision for greatest effectiveness.
Vision enhancement is a field of technology which is able to restore, vision, to those who have lost it.
However, the field is not solely focused on those who are blind. A recent development in the field has allowed those who are colour-blind to see the world in the same way that everyone else sees it.
LVES (low-vision enhancement systems) allow images to be projected inside a headset placed in front of the user's eyes. An example of its use includes helping the visually impaired.
NVE (night vision enhancement) uses infrared light to enable an image to be seen in apparent darkness; it makes use of an image intensifier tube which converts light into electrons - these electrons collide with a phosphor-coated screen resulting in an image. This technology is used by the military when identifying objects at night.
Robotics
Robotics is the creation of computers that perform tasks that humans cannot or are less efficient at performing.
Robots can be beneficial:
They can be used to complete mundane and repetitive tasks, removing the need for humans to do them.
They can be used for tasks that may possibly be dangerous to humans or require presence in a dangerous atmosphere, such as in a chemical factory.
Robots can cause issues:
Humans are replaced by robots to do certain tasks. This takes away jobs from people, and often their livelihood.
Many people get scared by the ability of robots, especially when they are equipped with artificial intelligence. They fear that robots could begin to overpower human beings.
Robots cannot respond with any kind of emotion.
Quantum Cryptography
Quantum cryptography is thought to be one of the safest ways to encrypt data. Most encryption methods use mathematics and algorithms to encrypt data. Quantum cryptography uses physics.
The key in quantum cryptography is made up of a stream of light particles that individually vibrate in all different directions. Creating these different vibrations is called polarising. Once transmitted, the light particles will then be passed through a filter that will reverse the polarisation and unscramble the data.
Computer Assisted Translation (CAT)
Benefits:
When in a foreign country, as long as internet connection is available, a person can quite quickly and easily translate words and phrases by entering them into a site such as Google Translate. This can improve their ability to communicate whith people in that country.
It can be used to translate whole documents and websites into a language of choice, quickly making it possible to read them.
Issues:
Sites such as Google Translate are designed to give direct translations, rather than the meaning behind the sentence.
One of the biggest issues is being able to restructure grammar across translations, picking the correct meaning of a word that has multiple uses, and also handling issues where there is no actual translation for the word in question.
3D and Holographic Imaging
Holographic imaging is the ability to make holograms. A hologram is a 3D image that is created with photographic projections. A hologram is a free-standing 3D image that you can see around. It does not need to mimic depth like a 3D image or virtual reality.
Virtual Reality
virtual reality is where a 3D space is made by a computer. The user is then effectively put into that 3D space by wearing some sort of technology, usually headset, which displays that space and their position within it.
Applications:
Games
Medical procedures make use of virtual reality by allowing doctorss to practice surgery. This can allow them to gain confidence and experience, and become more comfortable with procedures.
VR has been used in several training programmes, including flight simulators to give pilots experience in dealing with certain scenarios and in demonstrating military situations.
Issues:
Achieving calibration between the camera and user has not yet been perfected. Many users have mentioned issues with motion sickness because of the difference between what they feel and what they can actually see.
VR can also cause users to injure themselves if they are not in a large, empty space, as they could easily walk into objects and hurt themselves.
In some cases, users have experienced seizures because of VR, so epileptic users must be very cautious.
Unit 3 - Storage Devices And Media
What is backing up data?
Backing up refers to the copying of files and data to a different medium in case of a problem with the main storage device.
Why back up data?
Data could be lost due to failure of the original storage device (hardware failure)
Hackers may corrupt or even cause you to lose the data completely (viruses)
Might need backup if files need to be used elsewhere - original files are then protected against possible corruption or loss.
However, backups do not necessarily guard against the effect of a virus - the virus could attach itself to the files which could mean that the backups were also affected.
What is storage media?
It is the part that holds the data (hard disk, CD, etc.)
What is storage device?
The machine that reads/write data to and from the media.
Storage capacity
Storage capacity is the term given to the maximum amount of data that can be stored on the media.
Units of measurement
Storage amounts are measured in bytes and there are 8 bits in 1 byte.
Bits are short for "binary digits". This is the smallest unit of data that can be stored on the media.
1 bit
1 byte 8 bits
1 Kilobyte (KB) 2^10 bytes = 1024 bytes
1 Megabyte (MB) 2^10 KB = 1024 KB
1 Gigabyte (GB) 2^10 MB = 1024 MB
1 Terabyte (TB) 2^10 GB = 1024 GB
1 Petabyte (PB) 2^10 PB = 1024 PB
Storage capacity examples:
1 thousand characters (half a page of text) equals 1 kilobyte approx.
500 pages of text equal 1 megabyte approx.
Backing storage media
There are three different types of storage media and they all store data in different ways:
1. Magnetic backing storage media. Holds data magnetically. The surface area of the media is magnetised so that it can hold bits of data.
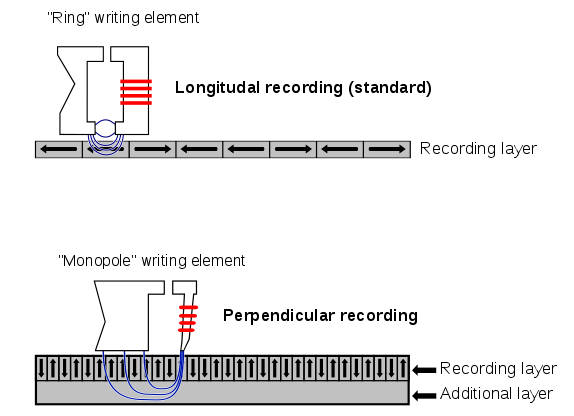
Examples:
Fixed hard disks and drives

Available on all computers and is the main method used for data storage.
Uses a read/write head to write and read data from it.
Disk surface coated with a magnetic film which is where the data is stored. Storage is done by altering binary codes to 1s or 0s.
Uses
Used to store operating systems and applications software.
Used for storing files (music, photos, videos, homework).
Used in file servers on computer networks to store files.
Advantages
Very fast data transfer rate and fast access times to data (saves data to disk and reads back from it quickly)
Very large memory capacities (can store thousands of movies and music files)
Disadvantages
Can be easily damaged
They lack portability
Portable and removable hard disks
Similar to hard disks but are usually connected via a universal serial bus.

Uses
Can be used as backup systems to prevent loss of data
Can be used to transfer data, files, and software between computers
Advantages
Data access time and transfer rate are very fast.
Large memory capacities.
Can be used to transfer information between computers.
Designed to plug into almost any computer via USB ports.
Disadvantages
Protective casing will only protect against minor bumps. If the device is dropped it can still become damaged.
Magnetic tape drive
Magnetic tape drives perform writing or reading of data.
Magnetic tapes
Magnetic tape is a thin strip of magnetically coated plastic which is wrapped onto a reel.
Data is stored on the magnetic plastic in the form of 1s and 0s (binary numbers)
Data is written to and read from in sequence (in order) which is also known as serial access.
This type of storage media has very slow data access rate.
Sony has developed magnetic tapes capable of storing a huge 185TB of data.

Uses
Used where extremely large amounts of data need to be backed up.
Used where the speed of reading/writing of data is NOT a priority.
Used for backups of computer networks in schools and business.
Advantages
Less expensive than the equivalent capacity of hard disk drive.
Very robust (not easily damaged)
Very large storage capacities.
Disadvantages
Very slow data access/transfer (reading data back from the tape is slow)
Needs another tape to update data.
2. Optical media. Holds data by burning dots onto the surface with a high powered laser. The device that reads the media can read the data by shining a lower powered laser over the dots.
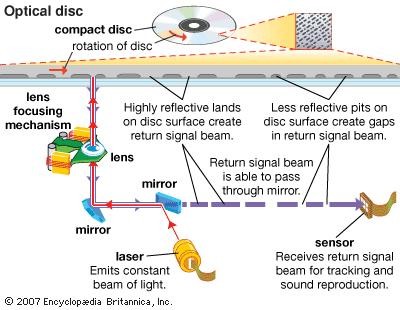
Examples
CD-ROM (Compact Disc - Read Only Memory) and DVD-ROM (Digital Video or Versatile Disc - Read Only Memory)
Data cannot be written over and can only be read. They are bought with pre-loaded data already on them.
CD-ROMs have a maximum capacity of about 800MB (about 400,000 pages of text)
DVD-ROMs have a maximum capacity of about 4.7GB (about 2.4 million pages of text)
Uses
CD-ROMs are used by manufacturers to store files such as: music tracks, software (word processor, spreadsheets, etc.), audiobooks, etc.
DVD-ROMs have much larger storage capacities (up to 4.7GB) than CD-ROMs and are used to store bigger files such as: movies, games, multimedia encyclopedias, etc.
Advantages
Less expensive than hard disc drives.
Data stored on them is 'read only' which means you cannot accidentally erase the files.
Very portable as they are small and light.
Disadvantages
Hold far less data than hard disk drives or pen drives.
Reading back from the disc is slow.
You cannot add your own files to the discs because they are read only.
CD-R and DVD-R
The letter R means that the disc is 'recordable' once only.
Once the disc has data recorded on it becomes a CD/DVD ROM (read only)
Data can be added to the disc (once) but not erased when it is on there.
Data is burnt onto the discs using a disc burner.
Thin layer of metallic dye is used to record the data onto.
When CD-Rs and DVD-Rs are burnt, the laser makes permanent marks (dots of data which represent 1s and 0s) onto the metallic dye.
These marks cannot be erased (which is why what you add to the disc is permanent)
DVD-Rs use a dye that allows for more dots to be burnt onto the disc's surface. This is why DVD-Rs can hold more data than CD-Rs
Uses
CD-Rs are used to create personalised playlists of music.
DVD-Rs are used to store home recordings of video shot on digital cameras.
They can be used to backup important data so that there are copies in case the originals get erased or deleted.
They can be used to transfer data from one computer to another.
Advantages
- Once burned, data is impossible to accidentally delete because the disc becomes read only.
- Cheaper than RW discs and hard disk drives.
- Easy to transport information from one computer to another
Disadvantages
- Only recordable once. This means that updating the disc is impossible.
- If an error occurs during burning, the disc is damaged and must be thrown away (wasted)
- Very slow data transfer rate (burning data onto a disc can take up to 15 min.)
CD-RW and DVD-RW
The letters RW stand for Re-Writable. This means that the disc can be recorded on over and over again.
Unlike CD/DVD-Rs these discs do not become read only once burned.
The dye used to record data is called 'phase changing dye' and it allows the bumps of data to be 'undone'. The bumps of data are really just flattened agin which effectively erases any stored data.
Data can be added to the disc and can also be erased.
Uses
CD-RWs are used to create personalised playlists of music and then add/remove songs as you wish.
DVD-RWs are used to record television programmes and can be recorded over many times.
Advantages
- Can be re-used many times.
- Data stored on the discs can be updated.
- Not as wasteful as the -R format.
Disadvantages
- More expensive to buy than CD/DVD-R discs
- It is possible to accidentally overwrite data (since RW discs can be updated)
- Data traansfer to the discs is very slow compared to a hard disk drive.
DVD-RAM (DVD-Random Access Memory)
With DVD-RAM writing and reading of data can happen at the same time. This means that you could watch a programme at the same time that another one is being recorded.
DVD-RAM discs can be rewritten over many times (over 100,000)
Data can be reliably stored on DVD-RAM for many years due to their high quality.
DVD-RAM has a capacity of 4.7GB.
Uses
- Because DVD-RAM discs last so long they are used in video and data archiving (safe store for important files and records)
- Used in DVD recorders to record TV programmes to allow simultaneous recording and playback.
- Used in camcorders to store video.
Advantages
- Long life, last at least 30 years.
- Can be written over 100,000 times.
- Very fast access to stored files.
- Offer very large storage capacity compared to CDs.
- Can read data at the same time it is being written.
Disadvantages
- Expensive compared to DVD and CD recordable discs.
- Don't work in as many devices as the -R or -RW discs.
Blu-ray discs
Work in a similar way to DVD-ROMs but the laser used to read the data is blue rather than red.
Blue lasers are capable of reading data dots that are positioned closer together on the disk surface. As a result, more data dots (1s and 0s) can be stored and read.
Uses
- Used to store high definition video (like high quality movies)
- Used in some home video consoles (like Playstation 3)
- Used to backup hard disk drives in PCs
Advantages
- Huge storage capacity, perfect for high definition movies.
- Data can be read/transferred very fast when compared to other optical media.
Disadvantages
- Very expensive compared to other optical media.
- Only work in Blu--ray drives/players which are expensive (not everyone has these drives which limits the use of the disks)
3. Solid-state storage.stores and retrieves digital information using onlyelectronic circuits, without any involvement of moving mechanical parts.

Any memory device with no moving parts and are based on electronic circuits.
Solid State Drives have no moving parts, no reels of tape, no spinning disks, no moving laser beams.
SSD technology is known as 'flash memory' and this is the smallest form of data storage. Examples include memory sticks, memory cards, etc.
They store data as 1s and 0s within millions of electrical transistors instead of on films of magnetic substance or as dots on discs.
If the transistor conducts an electric current, this equates to 1. If it does not conduct a currect, this equates to 0.
Advantages over magnetic disk drives
- Much smaller
- Use less power (no moving parts means less power needed)
- Faster data access and transfer times
- Much more robust (harder to damage)
Examples
Memory card

A memory card, flash card or memory cartridge is an electronic flash memory data storage device used for storing digital information. These are commonly used in portable electronic devices, such as digital cameras, mobile phones, laptop computers, tablets, digital pianos.
Pen drive, aka memory stick, USB stick
Solid state hard drive (SSDs)
Used in desktop PCs and laptops in place of magnetic hard disk drives.
Advantages
- Run silently
- Longer life span
- Faster data access and transfer times
- Use less power
- Produce less heat
Disadvantages
- Smaller storage capacity than magnetic hard disks.
- More expensive than magnetic hard disks.
Unit 4 - Networks And The Effects Of Using Them
What is a computer network?
A computer network is two or more computers that are connected together so that they are able to share resources, e.g. access to the internet, printers, file servers.
The connection between computers can be done via cabling or wirelessly through radio waves.
Computers not connected to a network are called "stand-alone" computers.
Types of network
1. LAN (Local Area Network)
Confined to a small area.
Usually located in a single building.
Uses cable to link computers.
Less expensive to build as equipment is owned by the organisation which is cheaper than renting lines and equipment.
2. WAN (Wide Area Network)
Covers a wide geographical area
Located in lots of different buildings and cities, countries, etc.
Uses more expensive telecommunication links that are supplied by telecommunication companies (e,g, satellite)
More expensive to build as sophisticated communication systems are used involving rental of communication lines.
3. WLAN (Wireless Local Area Network)
WLAN is a LAN where the computers are able to communicate with each other wirelessly.
Differences betwen a LAN and a WLAN
Advantages of a WLAN compared to a LAN:
WLAN is cheaper as there is less cabling needed.
It is very easy to link devices such as printers and scanners to the network.
You can work anywhere in the building in range of the wireless signal.
Disadvantages of a WLAN compared to a LAN:
There may be areas in a building where the radio signal is too weak.
There are security problems as the radio signals could be intercepted by hackers.
Wireless signals are not as reliable as wired cables and the data transfer speeds are not as high.
There can be interference from other electrical and electronic equipment used in the same building and this can disrupt the wireless signal.
Network devices
Network Interface Card (NIC)
NICs connect computers to a network.
There are two types of NIC:
Wired NIC

Wireless NIC

Each NIC has a unique physical address, known as the MAC (Media Access Control) address.
Hubs

Hubs are non-intelligent devices. When data gets sent to the hub, the hub simply sends the data to every computer or device on the network.
This means that every device on the network will receive the same data whether they requested it or not.
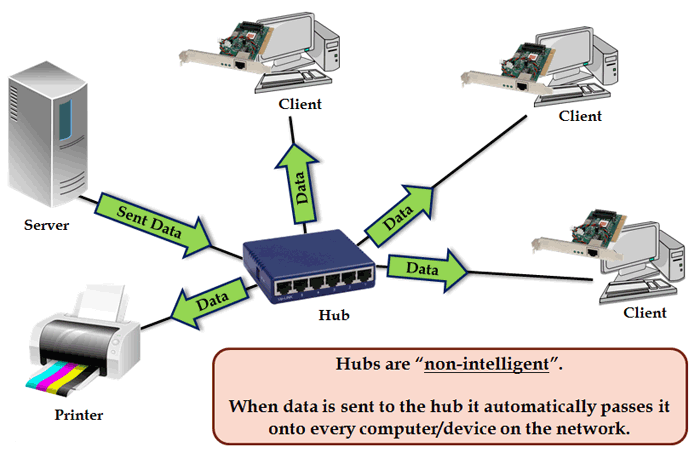
Switch
Switches, like hubs, connect computers and devices to form a network. However, switches are 'intelligent' devices.

Bridge
Bridges are used to connect LANs together.
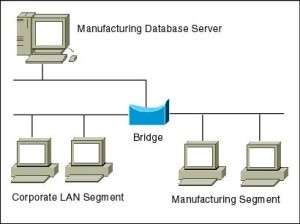
Modem
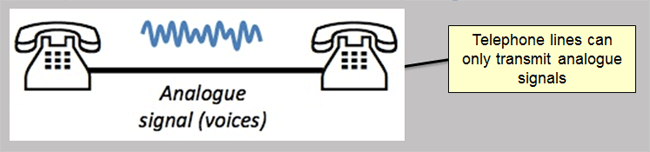
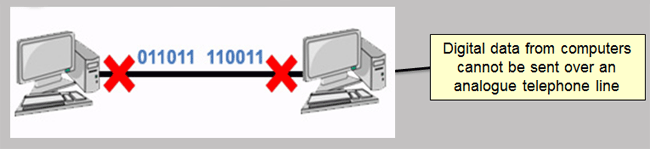
Modem stands for 'Modulator-Demodulator'
A modem converts the data from the computer (digital data) into sound (analogue data) that can be sent along ordinary telephone lines. Once the data arrives at the other end of the line, the sound will need to be converted back to digital data using another modem before it can be understood by the receiving computer.
Router
IP addresses
Each computer linked to the internet is given a number which is called its IP (Internet Protocol) address. An IP address looks like this: 123.456.1.98 and is unique for each device while linked to the internet.
Computers on the same network would share the same first few numbers of the IP address (this is used to locate the network)
Different devices on the same network are uniquely identified by the last few numbers of the IP address (this is used to locate individual devices on the network)
When data is transferred from one network to another the data is split into packets. The packets contain details of the destination address (IP) of the network it is intended for.
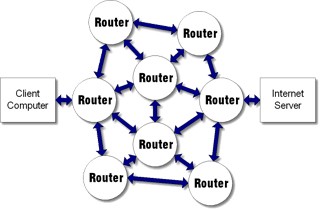
Routers are hardware devices that read the IP address (that the packages are carrying on) to determine the final destination of the packet.
Routers can be used to join several wired or wireless networks together. Routers are usually a combination of hardware which act as gateways so that computer networks can be connected to the internet using a single connection.
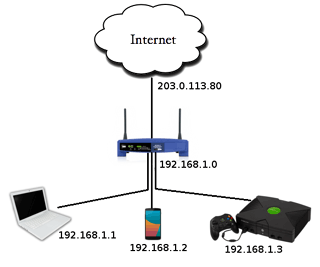
Images source:The ICT Lounge
How does a router store IP addresses?
Routers store IP addresses in something called a routing table.
The routing table lists all of the different routes to other networks.
The router will use the routing table to determine the best route to use when sending data to another network.
How does a router send data between computers?
Routers send packets of data between computers on different networks.
Each data packet contains the IP address of the computer/network that the data is being sent to.
The router will use the IP address to work out the best route in which to send the data to its destination.
The data will be received by routers on other networks which will read the IP address and re-route the data until it ends up at the exact device it was intended for.
Example of routing
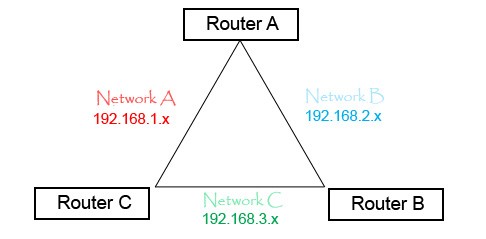
Routers don’t just route traffic to other networks, they learn which are the fastest routes and use them first. Using the above configuration, network A has two routes to network C; one directly through Router C (1 hop) and one through Router A then B (2 hops). When sending traffic from network A to C we obviously want it to try going directly through Router C first.This is the quickest and most efficient route but, how does the router know this? It knows by using something called a metric value. Each route the router knows of has a metric value assigned to it. A metric value is basically a preference number. If there are two routes to the same destination then the one with the lowest metric is assumed to be the most efficient. Routers will always use this route first until it fails, in which case it will then try the route with the next lowest metric and so on. Routers store all this information in a routing table.
The internet (INTERnational NETwork)
The internet is a huge group of networks joined together.
Advantages:
Huge amounts of information can be accessed almost anywhere.
Improved communication systems - this includes the use of text messages, emails, instant messaging, etc.
Changes in the way we shop - many people prefer to shop online.
VoIP (Voice over the Internet Protocol), enables cheap international phone calls to be made using the internet rather than having to pay for calls using a mobile or landline telephone.
Can help people with disabilities to be more independent, because they can order goods and services online.
Disadvantages:
Misinformation, there are many fake websites.
Cyber cryme, e.g. stealing personal information, bank account details.
Addiction to gambling, as there are many betting sites.
Increased problems due to hacking and viruses.
Paedophiles look for children using the internet.
The World Wide Web
The WWW is the group of web pages that are linked together using hyperlinks that allow us to access the information stored on computers.
Intranet (INTernal Restricted Access NETwork)
An intranet is a private network that is used inside an organisation and makes use of web pages, browsers and other technologies just like the internet.
Schools and colleges use intranets and they can hold all sorts of information from teaching resources, information about courses and adverts, to student personal records and attendance details. Parts of an intranet can be made available to anyone in the organisation, while parts that contain personal details can be made available only to certain people. Restriction to certain parts of the intranet is achieved by using user-IDs and passwords.
Difference between an intranet and the internet
An intranet contains only information concerning a particular organisation that has set it up, whereas the internet contains information about everything.
Intranets are usually only used by the employees of a particular organisation, whereas the internet can be used by anyone.
With an intranet, you can block sites which are outside the internal network using a proxy server.
An intranet can be accessed from anywhere with correct authentication.
Advantages of using an intranet
Intranets are ideal in schools because they can be used to prevent students from accessing unwanted information.
The internal email system is more secure compared to sending emails using the internet.
Only information that is relevant to the organisation can be accessed and this prevents employees accessing sites that are inappropriate or which will cause them to waste time.
The use of Wi-Fi and Bluetooth in networks
Wi-Fi
Wi-Fi enables computers and other devices to communicate wirelessly with each other. Areas, where the internet can be accessed wirelessly using Wi-Fi, are called access points or hotspots and they can be found in many public places, such as coffee bars, hotels, airports, etc.
The range of Wi-Fi depends on the type of wireless router being used and also if there are obstacles such as walls in the way of the signal. For a home network, the range of Wi-Fi are typically 50m indoors and 100m outdoors.
Advantages of wireless communication:
- You are not confined to working in the same place. For example, you can work on trains, buses and even some aircraft provided there is a signal.
- No trailing wires to trip over.
- It is easier to keep a working area clean if there are not as many wires in the way.
- There are no network wires so there are no costs for their installation.
Disadvantages:
- The danger of hackers reading messages.
- There are areas where you cannot get a wireless network.
- There is some evidence that there may be a danger to health.
- Limited signal range.
Bluetooth
Bluetooth is a wireless technology used to exchange data over short distances and it makes use of radio waves. The range of Bluetooth depends on the power of the signal and can typically be from 5m to 100m.
Uses:
- Wireless communication between input and output devices. If you have a wireless keyboard and mouse then they could use Bluetooth. Printers can be controlled wirelessly from a computer using Bluetooth.
- Communication between a wireless hands free headset and a mobile phone. People can use these while they are driving.
- Creating a small wireless network where the computers/devices are near to each other and where the small bandwidth is not a problem. For example, creating a small home wireless network.
- Transferring data between a computer and a mobile device such as mobile phone or tablet.
- Communication using a games controller. Many games consoles use Bluetooth.
Setting up and configuring a small network
Here are the steps you generally need to take to set up and configure a small network:
Choose an Internet Service Provider (ISP), pay them a subscription charge and get a router, often provided by the ISP (which might include wireless access point).
Connect the router to the telephone line or cable point (In some countries, this is a connection to a satellite link).
Connect any cabled devices to the router using wires between the ports on the router and the NIC on the device.
Connect any wireless devices, e.g. laptops, tablets, printers using wireless network. You will need to open settings in your operating system on each device to create a new connection. You usually need the password given to you by the ISP to do this.
You will need a browser on each device to access the internet.
Web browser software. What does it do?
A web browser is a program that allows web pages stored on the internet to be viewed. Web browsers read the instructions on how to display the items on a web page which are written in a form called HTML (Hypertext Markup Language).
A web browser allows the user to find information on websites and web pages quickly and it does this through:
- Entering a web address (URL)
- A web/internet portal
- Keyword searches
- Links
- Menus
Web browser software includes email software that allows you to send and receive email.
Access to an Internet Service Provider (ISP)
Connecting directly to the internet is very expensive and only suitable for large companies and organisations. Most people connect to the internet via an organisation called an Internet Service Provider. This is an organisation that supplies the connection to the internet as well as providing services including:
- Storage on their servers, where you can store your website
- Email facilities
- Instant messages where you can send short messages to your friends when they are online
- Access to online shopping
- Access to news, sport, weather, financial pages, etc.
When you establish a network connection with an ISP and pay their subscription charge they generally supply you with a wireless router. This will enable you to link devices wirelessly, thus forming a network that will allow users to:
- Share internet access
- Share access to hardware devices such as printers and scanners
- Share access to files held on different computers
At the back of the router, you will see more sockets into which Ethernet cables can be connected. You can connect part of your network to the router using cables rather than wirelessly.
The advantages and disadvantages of using different types of computer to access the internet
The internet can be accessed by a wide variety of devices from desktop computers to smartphones. Each device has its advantages and disadvantages over other devices for accessing the internet.
Using a smartphone to access the internet
Advantages
The internet can be accessed anywhere provided there is wi-fi or a mobile signal.
Encourages users to socialise with the social networking applications.
You can stay connected while moving around.
Disadvantages
Smartphones are not easy for parents to police. It is possible that children could access unsuitable content or arrange to meet up with strangers.
The websites are often a trimmed down version for smartphones and do not have the full capabilities of the full website when used with a laptop or desktop computer.
The small screen and keyboard can be frustrating to use compared to tablets, laptops or desktops.
As the smartphone is usually carried all the time, the frequent checking of email and internet applications may take time and attention away from interpersonal relationships.
Using a tablet to access the internet
Advantages
Tablets are smaller and lighter than most laptops and desktops which makes them easier to carry.
Tablets have larger screens compared to smartphones which makes using the internet easier.
Tablets are easy to use when standing up, making them useful for accessing information about places of interest, galleries, etc., when you are visiting them.
Disadvantages
Tablets have smaller screen than most laptops and desktops so it is hard to see a page without the need to scroll it.
Tablets come with a virtual keyboard which is not as easy to use as real keyboards used with laptops and desktops.
The awkward position in which tablets are used may lead to future health problems.
Using a laptop computer to access the internet
Advantages
Designed to be portable so they are smaller and lighter compared to a desktop computer.
Has a fairly large screen which makes reading web pages easier than reading the same pages on a smartphone or tablet.
Has an almost full-sized keyboard which makes typing search conditions easier.
Can be used when a flat surface is not available to use a mouse.
Disadvantages
Not as portable as a smartphone or tablet because of its size and weight.
The screen and keyboard are attached, which may lead to incorrect posture being used which can cause a backache or other health problems.
Using a desktop computer to access the internet
Advantages
A full-size keyboard and mouse make it easier to type search criteria and make selections.
The majority of web pages are designed to be viewed using a desktop and this enables the pages to be viewed as the website designed meant them to be viewed.
Desktop computers are better ergonomically because the monitor can be adjusted to the correct height and the keyboard and mouse are easier to use. This means there will be fewer health problems caused by their use.
Disadvantages
Desktop computers are not portable as they are large and heavy.
Desktop computers are hard to use while standing up.
Network issues and communication
Security issues regarding data transfer
Here are some of the ways security of a network can be breached:
Password interception
Here a person's password, which should be kept secret to them, becomes known to others. This means that other people can now sign in using their password and gain access to their files. When using the internet you can have lots of different passwords such as those for your email, bank accounts, stores, etc. If people know these passwords then they could read your emails, remove money from your bank account and purchase items using your details.
Virus attack
Viruses pose a major threat to networks. A virus is a program that replicates (copies) itself automatically and may cause damage. Once a computer or media has a virus copied onto it, it is said to be infected. Most viruses are designed to do something apart from copying themselves. For example, they can:
Display annoying messages on the screen.
Delete programs or data.
Use up resources, making your computer run more slowly.
Spy on your online use - for example, they can collect usernames, passwords, and card numbers used to make online purchases.
One of the main problems is that viruses are being created all the time and that when you get a virus infection it is not always clear what a new virus will do to the network. One of the problems with viruses is the amount of time that needs to be spent sorting out the problems that they create. All computers should be equipped with antivirus software, which is a program that is able to detect and delete these viruses. This should be updated regularly, as new viruses are continually being developed and would not always be detected by older versions.
How to prevent viruses
The best way to avoid viruses altogether is to use anti-virus software and adopt procedures which will make virus infection less likely.
Here are some steps which can be taken to prevent viruses entering a network:
Install antivirus software.
Do not open emails from unknown sources.
Keep antivirus software up-to-date. Configure the virus checking software so that updates are installed automatically.
Have a clear acceptable use policy for all staff who use computers.
Train staff to be aware of the problems and what they can do to help.
Do not allow programs such as games, video or movies to be downloaded onto the orgnisations's ICT systems.
Do not open file attachments to emails unless they are from a trusted source.
If possible, avoid users being able to use their own removable media (pen drives, portable hard disk drives)
Hackers accessing the network
Hacking is the process of accessing a computer system without permission. Hackers often access a network using the internet. In most cases the hacker will try to guess the user's password or obtain the password another way; for example, by using a cracking program which will generate millions of different passwords very quickly trying each of them in turn.
Sometimes special software is installed on user's computer without their permission and it can log the keys that the user presses, which can tell a hacker about usernames, passwords, emails, etc. This software is called spyware or key-logging software.
Use a firewall. A firewall is hardware, software or both that will look at the data being sent or received by the computer to either allow it through or block it. It logs the outgoing data leaving the network and incoming data from the internet. It therefore prevents access to the network from unknown IP addresses and it can prevent users from accessing unauthorised sites. It also warns a user if software is trying to run a program on the computer without the user's permission.
Use anti-spyware. This is special software that you run on your computer which will detect and remove any spyware programs that have been put on your computer without your knowledge with the purpose of collecting passwords and other personal information.
Change passwords regularly, if someone does manage to obtain your passwords. If they are changed on a regular basis at least they will only have the use of your passwords for a short while.
Protecting access by using user-IDs/usernames and passwords
System security is making sure that only authorised people access a computer system. This is called user authentication and it is normally carried out using a system of user identification (i.e. user-IDs) and passwords. Most computer operating systems provide systems of user-IDs and passwords.
Identifying the user to the system: user-IDs
A user-ID is a name or number that is used to identify a certain user to the network. The person who looks after the network will use this to allocate space on the network for the user. It is also used by the network to give the user access to certain files.
The network manager can also keep track of what files the user is using for security reasons. Network managers can also track improper use of the internet using user-IDs.
Preventing unauthorised access to the system: the use of passwords
A password is a string of characters (letters, number, and punctuation marks and other symbols) that the user can select. Only the user will know what the password is. When the user enters the password, it will not be shown on the screen. Usually an asterisk is shown when you enter a character. Only on entry of the correct password will the user be allowed access to the network. Some networks are set up so that if someone attempts to enter a password and gets it wrong three times, the user account is locked. If this happens, the user should contact the network administrator to have the password reset, which may involve answering security questions.
Choosing a password - the difference between strong and weak passwords
Examples of weak passwords:
mypassword
Esther
Steve1234
A strong password does not need to be long provided it contains symbols, capitals, numbers and letters. Although strong passwords are not impossible to crack, most hackers would quickly move on to a different computer system where a weak password had been used.
A strong password should be a combination of letters (capital and lowercase), numbers, and symbols that have no relation to each other, just totally random such as 4Hp!9$R;
Examples of strong passwords:
S%7c&X
€D23&!uL
Authentication techniques
As weak password can be easily cracked, and strong passwords are hard to remember, there needs to be an easier way to allow users access to networks.
Many networks use magnetic stripe cards or other ID cards containing chips which are used to gain access to the network. These are still used in conjunction with passwords and usernames since the card or ID card could have been stolen.
Biometric scanning systems can be used rather than usernames and passwords to allow access. Retinal scanning uses the unique pattern on the back of the eye to recognise a person and fingerprint scanning uses the unique pattern on a person's finger to identify them. Face recogntion can be used to match someone trying to log onto the network with those people who are allowed access.
Iris scanning is another biometric method used for authentication and it uses the coloured area of the eye surrounding the pupil for identification. It has the advantage over retinal scanning in that it can be carried out using regular video cameras and can bee performed as far as two feet away and also on people who are wearing glasses.
Biometric methods have the main advantage in that there is nothing to forget such as a card or a code.
Encryption
If information needs to be sent over the internet or another network and it needs to be kept secure, then encryption should be used. Encryption scrambles the data while it is being sent and only the true recipient is able to unscramble it. Should the data be intercepted by a hacker, then the data will be totally meaningless.
The process of scrambling data, sending it over the internet and then deciphering it when it reaches the true recipient, is called encryption. This requires encryption and decryption keys.
Encryption should be used for:
Sending credit card details such as credit card numbers, expiry dates, etc., over the internet.
Online banking.
Sending payment details (bank details such as sort-code numbers, account numbers, etc.)
Confidential emails.
Sending data between computers when confidentiality is essential.
The principles of a typical data protection act
The widespread use of ICT has made the processing and transfer of data much easier and to protect the individual against the misuse of data, many countries have introduced a law called data protection act.
There are a number of problems in organisations holding personal data:
The personal data might be wrong, which means wrong decisions could be made.
The orgnisation may not take care of the personal data it holds so others may find out about it.
What is personal data?
Data about an identifiable person (i.e. the data must be about someone who can be identified by name, address, etc.)
Data about somone who is living.
Data that is more personal than name and address. For example, medical records, criminal records, credit history, religious or political beliefs, etc. are all classed as personal data.
The effects of wrong personal data
Your medical details could be wrong, meaning you get the wrong treatment - which could be life threatening.
Wrong decisions might be made; for example, you could be refused a loan.
Wrong exam results could affect you getting a job.
Rights of the data subject and the holder
The person about whom the personal details are held is called the data subject.
The person in the organisation who is responsible for the personal data held is called the data holder.
A data protection act is a law that protects individuals by placing oblilgations on the organisations who collect and process the data in the following ways:
Registration (also called notification). It requires anyone who uses personal data to register with the person who is in charge of the act/law. They must say what data they intend to hold and what they intend to do with it.
Individuals can see their own personal data.Anyone can apply to see the personal dat held about them. Organisations have to show it and if there is any wrong information, then it must be corrected. There are some exemptions where you would be unable to see the information held about you. For example, you could be a criminal and apply to see the information the police have about you.
Data must be kept secure and up-to-date. Data subjects (the people the data is about) could take to court an organisation that does not keep their personal data secure.
The right for a person to claim compensation. If data is processed unlawfully by an organisation then the person could take them to court and claim compensation.
Data protection principles
All data protection acts are different but a typical act would contain the following principles:
Personal data shall be processed fairly and lawfully.
Personal data shall be obtained only for one or more specified and lawful purposes, and shall not be further processed in any manner incompatible with that purpose or those purposes.
Personal data shall be adequate, relevant and not excessive in relation to the purpose or purposes for which they are processed.
Personal data shall be accurate and, where necessary, kept up to date.
Personal data processed for any purpose or purposes shall not be kept for longer than is necessary for that purpose or those purposes.
Personal data shall be processed in accordance with the rights of data subjects under this act.
Appropriate technical and organisational measures shall be taken against unauthorised or unlawful processing of personal data and against accidental loss or destruction of or damage to personal data.
Personal data shall not be transferred to a country or territory unless that country or territory ensures an adequate level of protection for the rights and freedoms of data subjects in relation to the processing of personal data.
Network communication
Physical fax
A physical fax consists of a single unit containing a scanner, modem, and printer. The document being faxed is scanned and then the modem converts the data from the scan into a series of sounds that are sent along a telephone line. To send the fax you need enter the number of the fax machine at the receiving end of the line. The modem at the receiving end converts the sounds back into data and the printer prints the fax out. When using a physical fax, only one fax can be sent or received at the same time.
Electronic/internet faxing
Electronic/internet faxing uses internet technology rather than a phone network to send a fax and it is not necessary for each fax to be printed. All you need to send or receive the fax is a computer or mobile device that has access to the internet.
Differences between electronic faxing and physical faxing
Electronic faxing requires the use of a computer network whereas physical faxing does not.
No additional phone line needed for electronic faxing.
All physical faxes are printed; with electronic faxes, you choose to print or not, thus saving ink and paper.
You do not have the cost of purchasing a physical fax machine.
Faxes can be sent and received from mobile devices.
More than one fax can be sent and received at the same time.
You do not have to pay for the cost of a phone call to send a fax.
An email is an electronic message sent from one communication device (computer, telephone, mobile phone, or tablet) to another. Documents and images in electronic form can be attached to an email. All web browser software has email facilities.
Advantage and disadvantages of using email compared to faxing
Advantages of using email:
Emails can be viewed without others seeing them. Faxes are usually printed out in an area shared by other employees so they can be seen by others.
Emails can be viewed on any portable device (computer, smartphone, etc.) that has internet access. Physical faxes can only be obtained using a fax machine.
The information in fax form is not normally a computer file and cannot be edited by the receiver.
The receiver's fax machine may be out of paper and this will prevent the fax from being received. With emails this problem does not arise.
Cheaper to use email. Sending a physical fax means you have to pay for the cost of the phone call as well as the cost of the paper and ink.
Disadvantages in using email:
Emails can be used to distribute viruses. Faxing does not spread viruses.
Faxed signed documents are usually legally acceptable whereas emails are not.
Video-conferencing
Video-conferencing allows two or more individuals situated in different places to talk to each other in real time and see each other at the same time. They are also able to exchange electronic files with each other and pass electronic documents around rather than paper documents. It allows people to conduct virtual meetings. If meetings need to be conducted between people in different sites or even countries, then a WAN is used such as the internet.
Desktop video-conferencing systems in addition to a PC include a video compression card, a sound card, a microphone, a webcam, and specialist software.
Advantages and disadvantages of using video-conferencing
Advantages
Less stress as employees do not have to experience delays at airports, accidents, road works, etc.
Improved family life, as less time spent away from home staying in hotels.
Saves travelling time.
Saves money as business does not have to spend money on traveling expenses, hotel rooms, meals, etc.
Improved productivity of employees, as they are not wasting time travelling.
Meetings can be called at very short notice without too much plannng.
More environmentally friendly as there are fewer people travelling to meetings. This cuts down on carbon dioxide emissions.
Fewer car journeys means fewer traffic jams and hence less stress and pollution.
Disadvantages
The initial cost of equipment, as specialist video-conferencing equipment is expensive.
Poor image and sound quality.
People can feel very sel-coscious when using video-conferencing and not communicate effectively.
Although documents and diagrams in digital form can be passed around, an actual product or component cannot be passed around.
Lack of face-to-face contact may mean a discussion may not be as effective.
If the delegates are in distant locations, the picture can be out of synchronisation with the speech, which can be distracting.
Web-conferencing
When-conferencing is a service that allows conferencing events to be shared using internet technologies with users who are in remote locations. Usually there will be one sender and many recipients so, for example, a training event could be conducted by one trailer and many trainees in various locations. Web-conferencing is used for training events, meetings, lectures, and presentations.
Using web-conferencing the following can be shared:
Text and images
Voice
Video
Audio-conferencing
Audio-conferencing involves conducting a meeting held by people in different places using devices that allow voice to be sent and received.
Policing the internet
Many people think that the internet should be policed because it contains so many undesirable sites, but others consider users should choose what information they access. The problem with policing the internet is that the internet is a global network and you would need agreement from all countries using it, which is highly unlikely.
Here are some of the arguments for and against policing the internet.
Yes, the internet should be policed:
Is is too easy for children to access pornography.
Films, TV & radio programmes are regulated so the internet should be regulated as well.
There is a lot of misinformation. Wrong information about a persoon could potentially ruin their life.
People can hide through the anonymity of the internet and say things that they would not say to someone's face.
Other activities such as driving a car, drinking alcohol, etc., are policed so the internet should be policed as well.
There are many undesirable sites which tell you how to make explosives, produce illegal drugs, etc.
No, the internet should not be policed:
To police the internet would require resources no law enforcement agency has.
It is up to people to decide what they want to read or look at.
What is allowed in one country is not allowed in another so you could not agree on what to police.
Free speech is a fundamental right and should not be removed.